As with the first and second part I have split the post to not get it too long.
Day 14 – Where’s Rudolph?
This day I will keep a lot shorter and basically just give some additional hints.
For the first task we go to reddit and open up a random profile of a user. Then we replace the username in the url to IGuidetheClaus2020. Then it only is a matter of clicking on Comments and you have the first url.
Read through the posts, the second gives you the next answer.
Robert is Rudolf’s creator. Googling for rudolf creator we will give you the third answer.
On his reddit comments he speaks about twitter (Q4) and testing his reddit username, we find it is the same. (Q5)
In his tweets he mentions a TV show and that aswers question 6.
For Question 7 we can use googles reverse image search and find out about the city.
Downloading the file and looking at the EXIF data of the image wil give us a location (Q8) and a flag.
Rudolf has posted a email address in his twitter bio. Putting that into https://scylla.sh/api (a search for data breaches) as search term email:rudolphthered@hotmail.com will give us his password.
Using the GPS exif data from his image in google maps, we find that he is staying in the Marriott in Chicago. Street number is in the hotel details.
Day 15 – There’s a Python in my stocking!
The first question of today can all be answered by running the code in the python interpreter True + True and the second one can be answered by reading the day’s description.
bool("False") we can put into the interpreter again and Question 4 is another one for the Description.
For the code analysis we could just put the code into the interpreter and see what comes out. But let’s look at the code more in detail.
x = [1, 2, 3] Creates a Variable names x with the array containing 1, 2 and 3
y = x Because python used pass by reference this creates a variable y that points to the same thing (the array in this case) as x
y.append(6) appends 6 to the array y and x are pointing to.
print(x) prints the array.
Day 16 – Help! Where is Santa?
Since it gives us easier access to the challenge, we are going to use the attack box again. Deploy it and the challenge.
Pulling up the page in the web browser without any ports (meaning on 80), does not work, so we have to find the correct port.
A quick nmap scan should do the trick.
root@ip-10-10-226-56:~# nmap 10.10.244.23
Starting Nmap 7.60 ( https://nmap.org ) at 2020-12-23 03:55 GMT
Nmap scan report for ip-10-10-244-23.eu-west-1.compute.internal (10.10.244.23)
Host is up (0.0026s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
8000/tcp open http-alt
MAC Address: 02:7D:17:61:1D:3D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.67 secondsNow we can pull up the site with the browser.

The site suggests finding the link to the API with a python script and you should do that for practice if you haven’t done much with python yet.
But we can also view source and search for api.
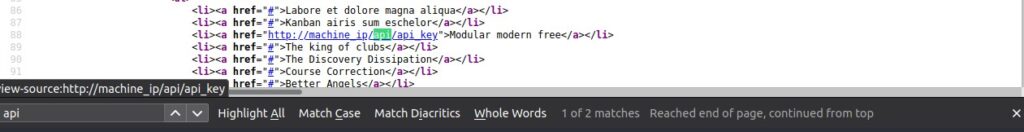
Accessing http://10.10.244.23:8000/api/ will give us a JSON response of: {"detail":"Not Found"}. We have to supply the API key. The challenge warns us that the server will block us after a certain amount of wrong attempts.
It also tells us, that the key is between 1 and 100 and odd. Which leaves 50 different keys to try.
Let’s write a python script to go through all potential keys:
# Importing the requests libary that allows us to do html requests
import requests
# We use a for loop to iterate over all potential API keys.
# We use the step size of two becasue of the info that the valid key is odd
for apikey in range(1,100,2):
# We make the request and store it in response. to concatonate a string
# (the api url ) with a number(the key) we need to convert the number to
# a string first
response = requests.get('http://10.10.244.23:8000/api/' + str(apikey) )
# now we print the text of the response
print(response.text)In the console output of that script we will find the answers.
Day 17 – ReverseELFneering
First we deploy both boxes. Once they are up, we ssh into the challenge box with the provided credentials.
I highly recommend that you do the example file1 walk through provided in the challenge to get used to the tools.
We open the challenge file in radare with r2 -d ./challenge1 and start the analysis with aa. This will take a while.
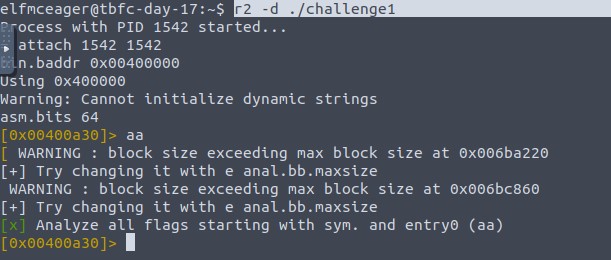
pdf @main shows us the content of the main function of the program.
In there we can already see what value is are stored in local_ch first.
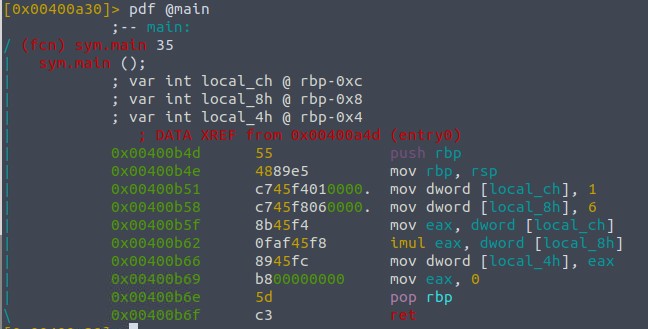
We can use two approaches here. the first is to go through the instructions and logically examine what should be in the variable asked for. But we can also use break points and step through the instructions, then look at the memory. We will use the later approach, even if the first would be faster in a simple program like this.
To find out what value is in eax when imul is called, we can set a break point at that function call with db 0x00400b62, then run the program up until the break point with dc.
Then we step through the instruction and look with px @eax at the memory content of eax.
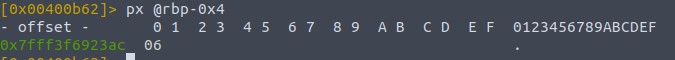
Stepping one instruction further, we can use px @rbp-0x4 to get the content of local_4h. We know local_4h is at @rbp-0x4 by looking at the top of main, where the variables are defined.
Day 18 – The Bits of Christmas
We start again with deploying the attack box and challenge. After giving it 5 minutes or so to start, follow the guide on how to connect to the windows remote desktop. Eventually you should see the Desktop.
We open up the TBFC_APP with ILSpy and can start browsing through the decompiled code.

Spotting the CrackMe portion, we dig further into that. It looks like this is where the form is handled. We are interested in the main form.
Let’s see what the code is the button will run when clicked:
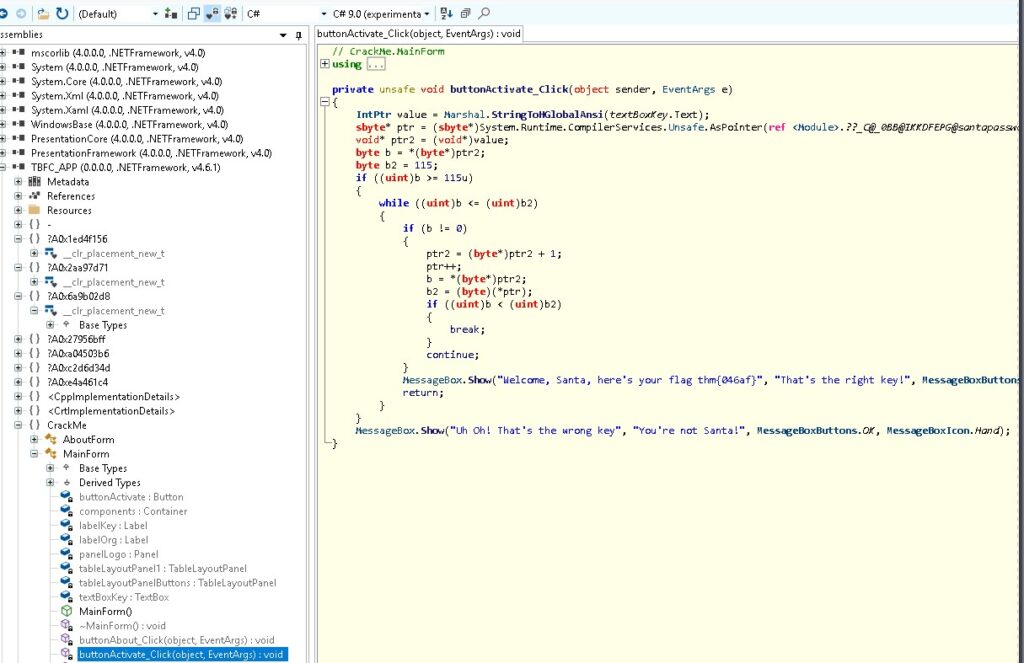
Looks like there is a password check in there and it references the correct password.
Further down is also the Flag that will be printed out if the correct password is supplied. This already answers the questions, but we can of course also run the program, supply the password and see the flag.


1 Pingback